Why understanding IAM (Identity and Access Management) Is Most Important For Better Cybersecurity.

The advances in modern technology have its pros and cons. For every app that you use to make your life better, you have the risk of getting your data exposed. Password stealing, hacking, and data breaches are now easier than ever.
Apart from that, there is also a threat called the ‘insider threat.’ There is where IAM becomes important. Unless you live under a rock for the past decade, you most likely have heard of Edward Snowden and the leaking of documents showing the NSA’s massive surveillance program. Furthermore, there have been many other instances of ‘insider’ attacks like Facebook, Coca-Cola, Tesla, and the one recently on Twitter.
An insider attack is an attack on an organization from people within the organization, such as employees who have access to the organization’s inside information like its security practices, data, and computer systems. It can be anyone, current employees, former employees, interns, business associates, or contractors.
4 types of insider attacks
Oblivious Insider
These are insiders who have access to sensitive data and have been compromised from the outside as they are being monitored and are oblivious to it.
Negligent Insider
These are insiders who are usually uneducated on potential security threats and are very vulnerable to social engineering attacks
Malicious Insider
These are insiders that carry out attacks like stealing data or destroying networks intentionally. This can be a disgruntled employee or a corporate spy.
Professional Insider
These insiders make a career out of exploiting company data and selling it on the DarkWeb.
So, how can we limit damages and protect data? That’s where Identity Access Management comes into the picture.
What is Identity Access Management (IAM)?
Identity Access Management (IAM) is a collective term that covers business policies, processes, technologies, and products that are used to manage user identities and regulate user access within an organization. IAM frameworks help IT, managers, to control user access to the critical data within the organization. IAM systems can either be deployed on-premises or can be provided by a third-party vendor through a cloud-based subscription model or deployed in a hybrid model.
IAM is a foundational security component, and its defined policies are
- How users are identified in a system;
- How their roles are identified in a system and how they are assigned to the users;
- Adding, removing, and updating individuals and their roles in the IAM system;
- Systems, information, and other areas protected by IAM;
- Assigning levels of access to individuals or groups of individuals; and
- The correct levels of protection and access for sensitive data, systems, information, and locations.
How does IAM work?
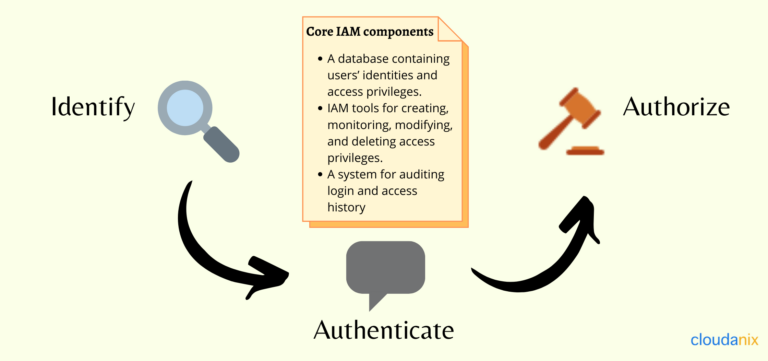
Key Definitions and Terms
Before we proceed, let us stop and look at some key terms you should know in the IAM space. I believe knowing these terms will give you comprehensive knowledge about what IAM is actually about
Access management
Access management includes various technologies for controlling and monitoring network access. Access management features include authentication, authorization, trust, and security auditing
Biometric authentication
This type of security process and technology that uses the user’s unique characteristics for authentication. Fingerprint sensors, iris and retina scanning, and facial recognition are examples of biometric authentication.
Context-aware network access control
Context-aware network access control is a policy-based method of granting access to network resources according to the current context of the user seeking access. For example, a user attempting to authenticate from an IP address that has not been whitelisted would be blocked.
De-provisioning
De-provisioning involves the removal of identity from an ID repository and terminating its associated access privileges.
Digital identity
Digital identity includes the ID itself, which includes the description of the user and his/her/its access privileges.
Entitlement
Entitlement specifies the access rights and privileges of an authenticated security principal.
Identity lifecycle management
It involves different processes and technologies for maintaining and updating digital identities. These technologies include identity synchronization, provisioning, de-provisioning, and the ongoing management of user attributes, credentials, and entitlements.
Identity synchronization
Identity synchronization is the technique of ensuring that multiple identity stores contain consistent data for a given digital ID.
Multi-factor authentication (MFA)
When authentication takes place using more than just a single factor, such as a username and password, for a system/network, then it is known as multi-factor authentication. At least one additional step is also required, such as receiving a code sent via SMS to a smartphone or satisfying a biometric authentication.
Password reset
Password reset is a feature that allows users to establish a new password, replacing their old ones. An added advantage of this is that it relieves the administrators of the job, and cutting support calls.
Privileged account management
This term refers to managing and auditing accounts and data access based on the user’s privileges. In general terms, because of his or her job function, a privileged user has been granted administrative access to systems. A privileged user, for example, would be able to set up and delete user accounts and roles.
Provisioning
Provisioning is the method of creating identities and defining their access privileges, and adding those identities to an ID repository.
Risk-based authentication (RBA)
Suppose a user attempts to authenticate from a geographic location or IP address that is not previously used by them then they may face additional authentication requirements. This method of dynamically adjusting the authentication requirements is known as risk-based authentication.
Security principal
A digital identity with one or more credentials that can be authenticated and authorized to interact with the network
Single sign-on (SSO)
Single sign-on is a type of access control for multiple related but separate systems. In SSO, you can access the system with a single username and password and without having the need to use different credentials.
User behavior analytics (UBA)
UBA technologies examine patterns of user behavior and automatically apply algorithms and analysis to detect important anomalies that may indicate potential security threats. UBA differs from other security technologies, which focus on tracking devices or security events. When UBA is grouped with entity behavior analytics, it is known as UEBA.
Benefits of IAM

Why is IAM important?
According to recent surveys and research, 80% of data breaches are due to weak or mismanaged credentials. I believe this alone is enough to highlight why IAM is so crucial in today’s world for every organization. IAM helps protect against security breaches by allowing administrators to automate numerous user account-related tasks.
Unless you want to pay fines, you should implement IAM. IAM is a key step in implementing GDPR and HIPAA. Meeting compliance requirements will not only help your business thrive but also give it authenticity. You are likely to attract customers if they know you implement security controls like IAM.
The more security feature options you have, the better. IAM, which has an ever-increasing list of features — including biometrics, behavior analytics, and AI — is well suited to the rigors of the new security landscape. Also, using a checklist to ensure your IAM policies and procedures have not lapsed is essential.
Why Cloudanix?
Cloudanix (www.cloudanix.com) provides you with the IAM recipe that does regular audits and notifies you if you have any of the above AWS IAM misconfigurations. To explore our AWS IAM audit recipe, you can start by signing up for a free trial.