What is Multi-Factor Authentication (MFA)?

Most organizations require their employees to use multi-factor authentication (MFA) solutions these days. This is because your traditional passwords are not secure anymore. Think of this, between your sensitive data and a hacker, the first and only line of defense is your password. Over the years, hackers have become steadfast in developing better password cracking tools and sophisticated phishing attacks to steal credentials and get unauthorized access to private user accounts.
Consider Google. One password is linked with your Gmail account, your Android device, YouTube, and any other web apps that you use your Google Account to connect with, like social media sites like Facebook, Twitter, and so on. And this is just on a small scale. Hackers have employed these methods in causing massive data breaches in various companies, banks, government agencies, and healthcare organizations. Recently, the engineers at Microsoft said that using MFA can block 99.9% of the account hacks. With the growing risks, many companies and compliance standards make it mandatory to implement Multi-Factor Authentication.
In this post, we will cover the following
- What is multi-factor authentication?
- How does multi-factor authentication work?
- The different methods to achieve multi-factor authentication
- Why do multi-factor authentication solution makes us secure
What is Multi-Factor Authentication (MFA)?
Multi-Factor Authentication or MFA is an authentication method requiring the user to provide two or more security verification checks to prove their identity for access to an account or a transaction. In other words, with MFA, the password isn’t just your only line of defense. You will use different methods like biometrics, one-time passwords, or PINs to verify your identity before gaining access to an online resource. MFA forms an exceptionally fundamental component in any identity and access management (IAM) policy.
How does Multi-Factor Authentication Work?
Below is an infographic showing how multi-factor authentication works.
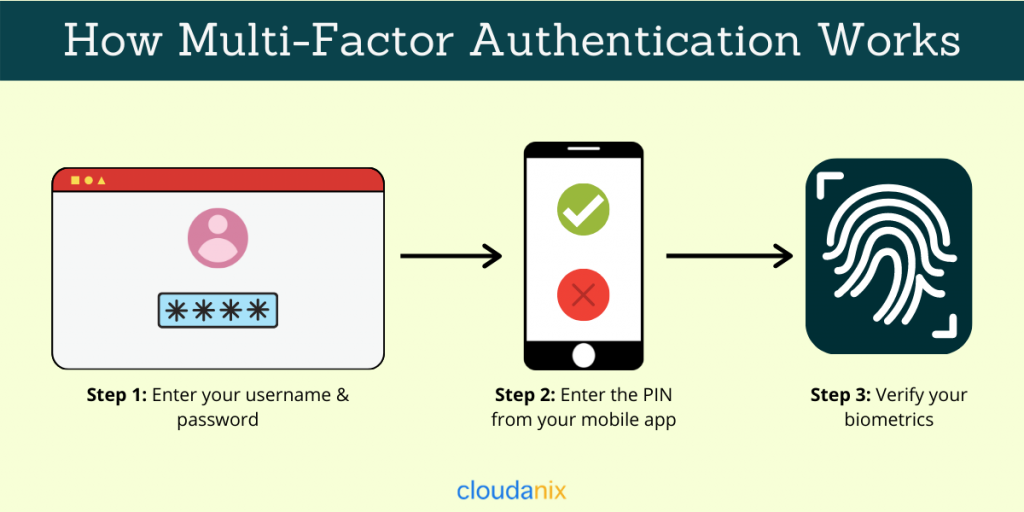
As I explained earlier, Multi-Factor Authentication adds more lines of defense in the form of additional verification information (factors) to prevent unauthorized access to your resources. The most common multi-factor authentication factors that users encounter are one-time passwords (OTPs), personal identification numbers (PINs), or biometrics like fingerprints. After entering your user name and password, you will have to prove your identity in one or more ways with any of the solutions you or your organization employed.
Multi-Factor Authentication Methods
The three most common methods to verify the user’s identity are based on the following three factors:
- The Knowledge Factor or the things you know. Examples of this method using one or a combination of personal identification numbers (PINs) or a personal security question.
- The Possession Factor or the things you possess. Examples of this method use one-time passwords (OTPs) generated by SMS, email, or smartphone apps; software security tokens, or smart cards.
- The Inheritance Factor or the things you inherit. Examples of the methods in this are biometric methods like fingerprint scan, facial recognition, voice recognition, retina or iris scanning, etc.
Importance of Multi-Factor Authentication (MFA)
- Protection Against Identity Theft: There are various methods by which hackers can steal your passwords. Three of the most common methods used by attackers to steal passwords are – keylogging, which involves secretly recording the keys struck on a keyboard; phishing, which involves fraudulently asking the victim for sensitive information via email, SMS, or a phone call; and pharming, which involves the installation of malicious code onto a device that redirects users to a fraudulent website where they enter sensitive information. It can significantly reduce breaches due to identity theft.
- Protection Against Weak Employee Passwords: You can’t have control over what passwords employees keep. Many studies show that employees often keep weak passwords like “password12345” and so on. These passwords are very easily stolen. Since you can’t control what password an employee sets, you can always employ multi-factor authentication to make your organization secure.
- Adhering to Compliance Standards: With the number of breaches and leaks, regulatory authorities and legislators have taken action and demanded that organizations meet specific security demands. Multi-factor authentication is one of them. In the financial sector, compliance standards like SOX and PCI DSS make it mandatory to use MFA or 2FA (Two-factor authentication). In the healthcare sector, while it is not explicitly mentioned, under HIPAA, healthcare organizations need to put measures in place to enforce password security. This may include multi-factor authentication. Finally, to be NIST and CIS compliant, you should implement MFA.
- Protecting Small Businesses from Cyber Attacks: Small businesses are being targeted at a growing rate by hackers. MFA can significantly reduce this. Since MFA is simple and relatively easy for small organizations to roll out, it is a game-changer when protecting small businesses from cyber attacks.
- Cyber Attacks are not just data breaches: Cyberattacks include destroying or leaking data, damaging an organization’s infrastructure, using accounts for propaganda, damaging someone’s reputation, and so on. Employing MFA can significantly block all kinds of cyberattacks.
How Can Cloudanix Help?
By now, you must have understood what multi-factor authentication is and why it is crucial. At Cloudanix, we have several audit rules for GitHub and cloud services like AWS and the Google Cloud Platform that check if you have implemented multi-factor authentication at various levels in your organization. You can sign up for a free trial!