As A Cloud User, Should I Be Worried About Cloud Compliance?
Introduction
How about we start by understanding “What Cloud is” and then move to “Cloud Compliance”? Servers that are accessible over the Internet, as well as the software and databases that run on them, are known as “the cloud.” Cloud computing has transformed the way businesses operate and scale, making it a universal feature – whether you’re a big corporation using cloud services or a consumer whose data is stored on these companies’ servers.
Storing almost all of your data, applications, services, and resources in the cloud can expose your company to threats. An important aspect of cyber security is cloud security and cloud compliance, which protects cloud computing systems. This will keep data private and safe across all the platforms that work online.
As the owner of all your critical databases, you must confirm if your data is secure. You can do this easily by checking with your Cloud provider. You can easily do this as part of your regular audit to check that your data is secure.
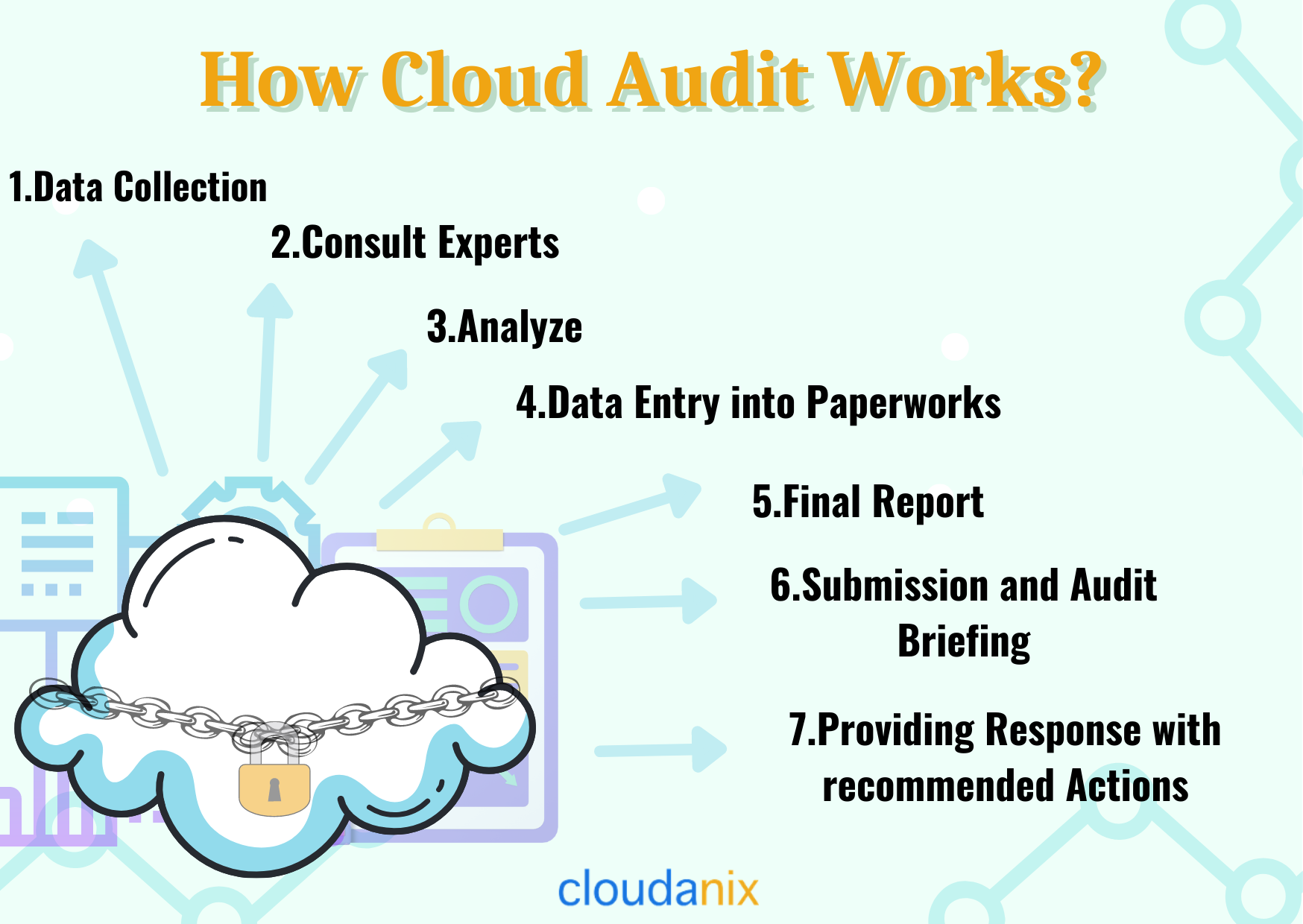
What is Cloud Audit?
A Cloud audit is similar to any other audit, however, its main focus is on the nuances of cloud environments. The purpose of cloud computing audits is to determine whether cloud workloads are using best practices, complying with appropriate standards, and complying with certain benchmarks when offering services. The dynamic nature of software-as-a-service (SaaS), infrastructure-as-a-service (IaaS), and platform-as-a-service (PaaS) environments in the cloud increases the importance of auditing and compliance.
The audit is carried out by a cloud auditor, which is a third party that can examine controls of cloud services independently with the intent of expressing an opinion. By reviewing objective evidence, audits verify adhesion to standards. In terms of security controls, privacy impacts, and performance, a cloud auditor can evaluate the services offered by a cloud vendor. Security auditing can determine whether or not the security controls implemented in the information system are implemented correctly, are working as intended, and are producing the desired outcome. The auditor can also conduct an assessment of the security requirements for the system.
- Data Collection: Collect as many pieces of evidence and documents as possible.
- Consult Experts: Talking with the professionals working with the cloud service providers to understand the working much better.
- Analyze: Validate the process to see if it acts in accordance with CSA (Cloud Security Alliance) and ISACA (Information Systems Audit and Control Association) controls.
- Data Entry into Paperworks: Prepare a report with recommendations based on an analysis of documentation and interviews.
- Final Report: A detailed audit briefing and documentation submission are scheduled with the company/organization.
- Submission and Audit Briefing: Discussion of the final report and recommendation of actions with the management.
- Providing Response with Recommended Actions: Taking appropriate action.
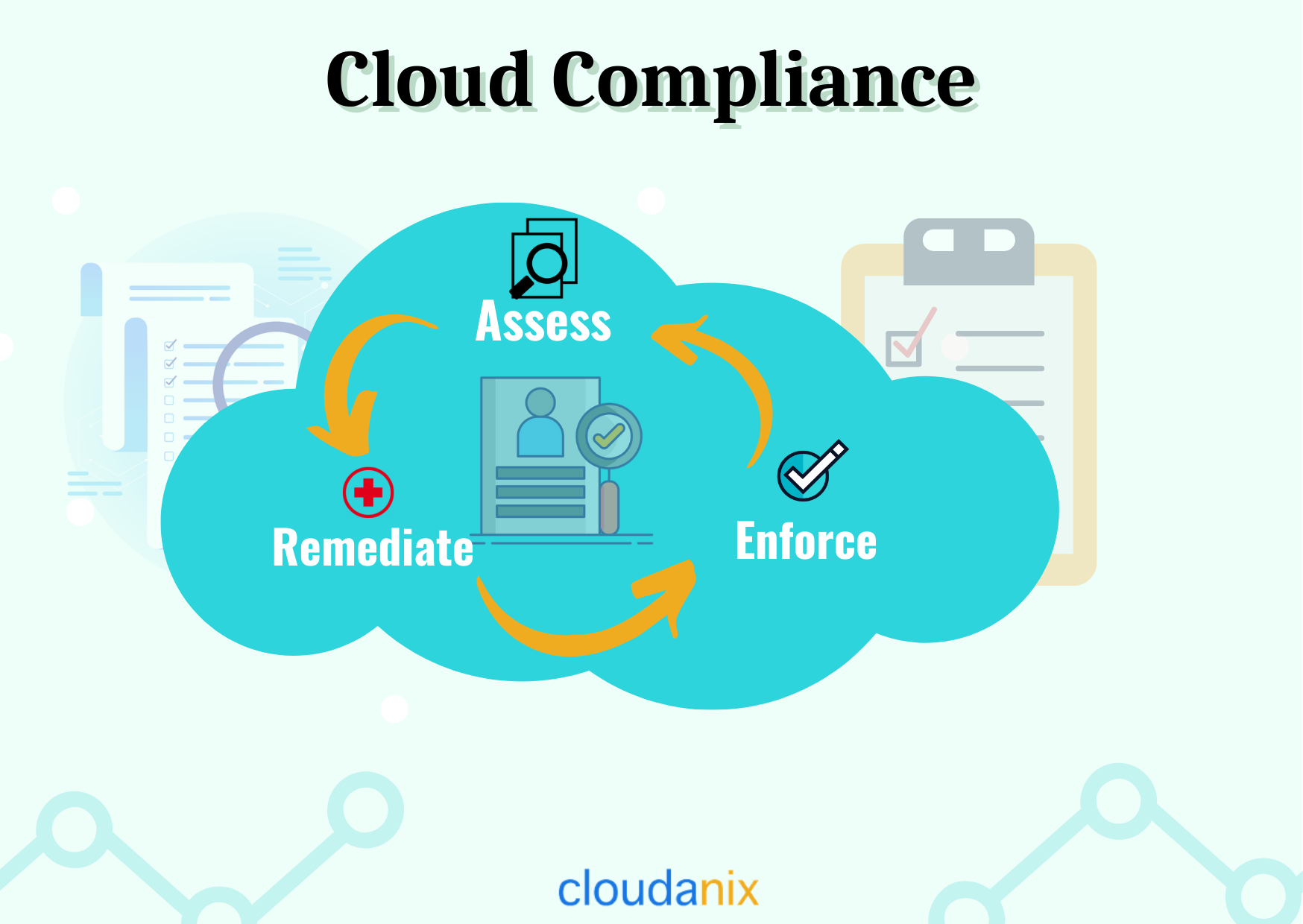
Cloud Compliance ensures that cloud computing services meet compliance requirements. It’s crucial for a company/organization to be compliant with global regulations. Regulations related to your cloud include HIPAA (Health Insurance Portability and Accountability Act), ISO 27001, NIST (National Institute of Standards and Technology), etc.
Cloud Compliance standards have evolved as cloud security adoption has increased since cloud platforms and services need to comply with a variety of international, federal, state, and local security standards, regulations, and laws. In addition to legal challenges, fines, penalties, and other negative consequences can result from non-compliance with these rigid rules.
It is the responsibility of the cloud user (the company using the cloud) to make sure the company is abiding by the compliance rules and regulations. The slightest mistake can lead to your brand being damaged. Hence, they must be guided by applicable laws and regulations. Whether your business is a part of compliance or not, your duty as a business is to follow the best practices ensured by these audits.
Consider a SOC2 control example:
NIST-800-53 AU-3 says “The information system generates audit records containing information that establishes what type, when, where, the source and the outcome of the event occurred and the identity of any individuals or subjects associated with the event.”
In AWS, you can enable CloudTrail logging, while on S3 resources, you can enable Access logs.
Is Cloud compliance difficult to achieve?
So you might have a question, Is cloud compliance difficult to achieve? Not really. When you have the right tools and are committed to providing world-class service to your users, compliance is a breeze.
Well, for this you need not worry because Cloudanix is here to help you. Sign up for 2 weeks of free trial and assess your Cloud Security posture.