A Practical Step by Step Guide To Prevent Security Breach Of Your AWS Account

Amazon Rainforests, the world’s largest rainforest, is crisscrossed with several rivers, inhabits over a thousand types of flora and fauna. It is so densely populated with greenery that only the person knowing the exact right path can find it once something goes inside. In other words, it is secure. Probably Amazon Web Services got inspired by its namesake while building its robust security schemes. Let us dive into the several methods you can incorporate in your AWS working to stay safe from security breaches!
Let's start with the AWS IAM service
Create a strong password for your AWS resources and MFA
To help ensure that you protect your AWS resources, always set a strong password with a combination of letters, numbers, and special characters. Include Multi-Factor Authentication. It is a security capability that provides an additional layer of authentication on top of your user name and password.
Use a group email alias with your AWS account
In case you are unavailable to manage your AWS Cloud workloads, using a group email alias with your AWS account lets other trusted members of your organization manage the account in your absence.
Set up AWS IAM users and roles for daily account access
Use AWS Identity and Access Management (IAM) to create users, groups, and roles to manage and control access and permissions to your AWS resources. When you make an IAM user, group, or role, ensure it can access only to the AWS resources to which you explicitly permit it. If you are the account owner, it is recommended that you create an IAM user for yourself for the daily use of your resources.
Delete your account's access keys
You can grant access to your AWS resources from the command line or for use along with AWS APIs. However, it is recommended that you do not create or use the access keys connected to your root account for programmatic access. Delete all access keys. Create an IAM user and grant that user only the permissions needed for the APIs you plan to call. You can then use that IAM user to issue access keys.
Enable CloudTrail in all AWS regions
You can track all activity in your AWS resources by using AWS CloudTrail. In case you initially do not know how to use CloudTrail, AWS Support, and your AWS solutions, you can troubleshoot a security or configuration issue.
AWS S3 and EC2 are the most used services
Here are security measures that can be adopted specifically for these
Amazon S3 security guide
Simple Storage Service (S3) is one of the most popular AWS services and provides a scalable solution for objects storage through web APIs. S3 buckets can be used for many different usages and in many different cases.
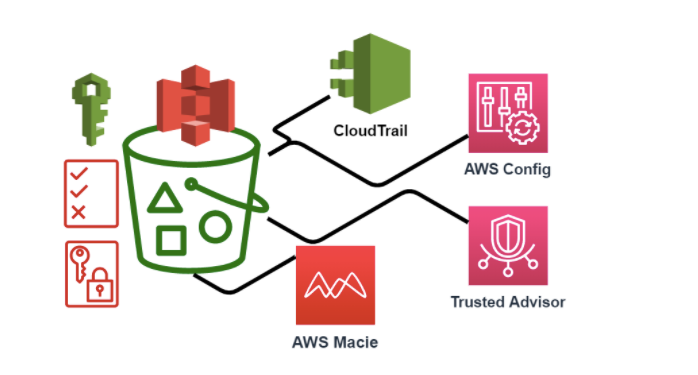
Here are some ways to protect your AWS S3 buckets
- Writing AWS User policies that specify the users that can access specific buckets and objects
- Writing bucket policies that define access to specific buckets and objects.
- Using the Amazon S3 Block Public-Access as a centralized way to limit public access. Block Public Access settings override bucket policies and object permissions. Be sure to enable Block Public Access for all accounts and buckets that you don’t want publicly accessible.
- Set access control lists (ACLs) on your buckets and objects.
- Be sure to review ACL permissions that allow Amazon S3 actions on a bucket or an object.
- Be strict about who gets Read and Write access to your buckets.
- Set up MFA-protected API access, which needs that users authenticate with an AWS MFA device before they call certain Amazon S3 API operations.
- If you temporarily share an S3 object with another user, create a pre-signed URL to grant time-limited access to the object.
- Enable Amazon S3 access logging. Use AWS Config to monitor bucket ACLs and bucket policies for any violations that allow the public to read or write access.
Finally, use encryption to protect your data. If the use case requires encryption during transmission, Amazon S3 supports the HTTPS protocol, which encrypts data in transit to and from Amazon S3. All AWS tools and SDKs use HTTPS by default. If your use case requires encryption for data at rest, Amazon S3 offers server-side encryption (SSE). The SSE options include SSE-S3, SSE-KMS, or SSE-C. You can specify the SSE parameters when you write objects to the bucket. There are other default encryption options on your bucket with SSE-S3 or SSE-KMS, which you can add to your system.
Amazon EC2 security guide
Elastic Compute Cloud (EC2) is another widely used service by Amazon. It allows us to rent virtual computers that can be used to run any arbitrary applications. AWS EC2 provides a scalable solution to rent and use a new computer, and manage its status via a web-based user interface. The user can manage every aspect of an EC2 instance from the creation and execution of the definition of access policies. It’s undeniable that AWS EC2 constitutes a powerful tool that will inevitably result in a security breach if not correctly configured and protected.
Few of the security measures in EC2 are
- Use multi-factor authentication (MFA) with each account.
- Use TLS to communicate with AWS resources.
- Set up API and user activity logging with AWS CloudTrail.
- Use AWS encryption solutions, along with all default security controls within AWS services.
- Ensure no backend EC2 instances are running in public subnets.
- Use advanced managed security services such as Amazon Macie, which assists in discovering and securing personal data stored in Amazon S3.
- Ensure no EC2 security group allows unrestricted inbound access to TCP ports 20 and 21 (File Transfer Protocol).
- Ensure no AWS EC2 security group allows unrestricted inbound access to TCP and UDP port 53 (DNS).
AWS provides a robust security system for your enterprise. These were some additional measures you can take from your side to ensure no data leakage of security breach affects your company. I hope this helps you and your enterprise!
How Can Cloudanix Help?
Cloudanix provides 1 click setup to perform continuous compliance checks and real-time monitoring of more than 500 rules and checks to help you stay secure and worry-free. We offer a very generous free trial which you can see for yourself how easy it is to stay secure and protect your customer’s data.