HIPAA Compliance - A Comprehensive Guide

HIPAA stands for Health Insurance Portability and Accountability Act which was passed in 1996. HIPAA was also known as Kennedy -Kassebaum Act. This is a United States federal statute enacted by the 104th United States Congress and was signed into law in 1996 by then-President Bill Clinton. This law was created to maintain the flow of healthcare information in a modernized way. Its main motive was to see how personally identifiable data was maintained and protected by the health organizations. It also ensured the elimination of waste, fraud, and abuse and that healthcare insurance industries must be protected from various thefts and frauds.
HIPAA necessitates that medical services offices (emergency clinics, facilities, and private practices ) that have access to Protected Health Information (PHI) make moves to guarantee patient information assurance. Anytime a medical building outsources a service, the service must be HIPAA compliant also. Altogether, both partners being HIPAA compliant results in exceptional data security. That’s why at Transcription Outsourcing, we understand the severity of knowledge breaches and are 100% compliant.
What is the purpose of HIPAA?
HIPAA sets a patient data protection standard. If a company handles sensitive protected health information (PHI), there are several regulations they need to follow. Hospitals, doctor offices, clinics, and all healthcare facilities must outsource their confidential files to compliant companies.
HIPAA is also known as Public Law 104-191. It has two primary purposes: to provide continuous insurance coverage for workers who lose or change their job and ultimately reduce healthcare value by standardizing the electronic transmission of administrative and financial transactions. Other goals include combating abuse, fraud, and waste in insurance and health care delivery and improving access to long-term care services and insurance.
What is PHI?
Protected Health Information (PHI) is considered our healthcare data. Under HIPAA, PHI is the health information like diagnostics, treatment information, prescription information, and medical test results that HIPAA tries to protect and keep private. Every single healthcare detail like Identification numbers and demographic information such as birth dates, ethnicity, gender, and contact information fall under the HIPAA protection.
The Need for HIPAA Compliance
This compliance is more critical than ever. HIPAA safeguards who can access and view the specific health data and restrict sharing that information with others. There are security rules to protect the privacy of individuals’ healthcare information. Anyone working as a healthcare specialist or having business with healthcare clients requiring access to health data must be HIPAA compliant.
Organizations that require HIPAA compliance include:
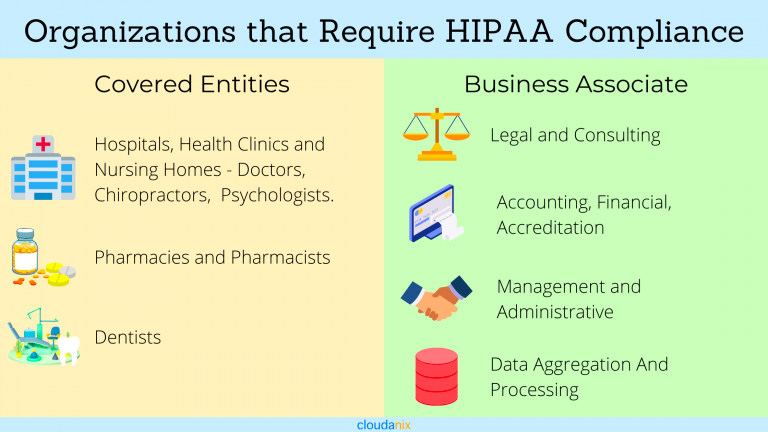
HIPAA compliance may seem inconvenient to some organizations, but others find the law terrifying. There are many reasons why this compliance is essential to a successful medical practice today. If any of these enterprises have business with others, they also require HIPAA compliance. For example, suppose they need outsourcing (translating, transcription, medical billing, coding, etc.). In that case, the medical provider or facility will be responsible if they have business with a legitimate medical transcription services company or a fraudulent foreign-based company.
HIPAA Rules
HIPAA Privacy Rule
Privacy Rule shows how healthcare providers can use patient data. It outlines what they can disclose without the patient’s permission and to whom and what they cannot. “Right to access” is also guaranteed to the patients. They can also obtain copies of their medical records and personal health information. Written privacy policies are required by healthcare providers for their organizations and to notify patients. It also says to provide annual HIPAA training to staff.
The information covered under HIPAA privacy rule:
- Names
- Birth, death or treatment dates, and any other dates relating to a patient’s illness or care
- Contact information: telephone numbers, addresses, and more
- Social Security numbers
- Medical record numbers
- Photographs
- Finger and voiceprints
- Any other unique identifying number or account number
HIPAA privacy rule is applied to covered entities ( Individuals and Organizations):
Health Care Providers
- Doctors
- Clinics
- Psychologists
- Dentists
- Chiropractors
- Nursing homes
- Pharmacies
- Health Plan
Health insurance companies
- HMO’s
- Company health plans
- The government provided health care plans
Health Care Clearinghouse
- These entities process healthcare data from another entity into a standard form.
HIPAA Omnibus Rule
The Omnibus Rule elaborates on the role of Business Associate Agreements (BAAs) to include subcontractors, consultants, storage companies, and many more organizations and individuals. Previously this was not included in the HIPAA rule.
The changes increased the civil penalties for HIPAA violations. It also updated the breach notification rules. This rule also prohibits the use of genetic information for purposes of underwriting insurance policies. PHI cannot be used for a marketing purpose in this rule.
Here are a few requirements covered entities and business associates affected by HIPAA might need.
- Updating BAA to reflect the changes in the Omnibus Rule.
- Send new BAA copies and get them signed to stay compliant.
- Refresh your privacy policy
- Update the Notice of Privacy Practices
- Finalize your training to make your staff aware of all Omnibus rule adjustments.
- HIPAA Security Rule
The Security Guidelines for the Assurance of Electronic Ensured Wellbeing Data (ePHI) sets principles for defending patient information. This incorporates how that information ought to be dealt with, kept up, and sent.
The rule requires healthcare organizations to have three types of data security safeguards, administrative, physical, and technical safeguards.
HIPAA Security Rule has 3 Key security zones:
- Administrative
- Physical
- Technical
How Does the HIPAA Security Rule Protect Your Data?
HIPAA rules require covered entities to cling to specific authoritative interaction controls to guarantee and check their consistency with the HIPAA Security Rule:
- Security Management Process
- Assigned Security Responsibility
- Workforce Security
- Information Access Management
- Security Awareness and Training
- Security Incident Procedures
- Contingency Plan
- Evaluation
- Business Associate Contracts and Other Arrangements
- Facility Access Controls
- Workstation Use
- Workstation Security
- Device and Media Controls
- Access Control
- Audit Controls
- Integrity
- Person or Entity Authentication
- Transmission Security
- HIPAA Enforcement Rule
The Enforcement Rule enables HHS to uphold the Protection and Security Rules. It gives (Office for Civil Rights) OCR the position to examine HIPAA complaints, conduct compliance reviews, perform training and effort, and pay fines of up to $1.5 million. A year ago, (Office for Civil Rights) OCR punished 10 associations for a sum of $12.27 million. OCR likewise works with the Department of Justice to allude to potential criminal infringement of HIPAA.
HIPAA Breach Notification Rule
Breach Notification Rule requires HIPAA-covered entities and business associates to notify affected individuals of improper PHI access. This should be done within 60 days. It’s essential to recollect that regardless of whether ransomware scrambles ePHI, it’s viewed as a breach – and in this manner falls under the HIPAA break notice rule.
What Information is protected under HIPAA?
The Privacy Rule protects all individuals’ health information. It can be held in any form, including digital, paper, or oral.
PHI includes but is not limited to the following:
- Name of the patient, address, birth date, Social Security number, biometric identifiers, or other personally identifiable information.
- Any medical conditions from past, present, or future.
- Any help required by the individual
PHI does not include the following:
- Employment or educational records, as well as other records, are subject to or defined in the Family Educational Rights and Privacy Act (FERPA)
- De-identified data, meaning data that doesn’t identify or provide information that would identify a private — there are not any restrictions to its use or disclosure
- 5 Main Components
There are five sections to the act, known as titles.

The relevant section of HIPAA compliance for IT providers is HIPAA Title II. It is also known as the Administrative Simplification provisions.
Title II comprises the following five elements of HIPAA compliance requirements:
- National Provider Identifier Standard. Every healthcare entity must be assigned a unique 10-digit National Provider Identifier number or NPI. Healthcare entities include individuals, employers, health plans, and healthcare providers.
- Transactions and Code Set Standard. This protocol must be used in electronic data interchange (EDI) to submit and process insurance claims.
- Privacy Rule. This rule ensures national standards to protect patient health information. It is known as the Standards for Privacy of Individually Identifiable Health Information.
- Security Rule. The Security Standards for the Protection of Electronic Protected Health Information (ePHI) sets standards for safeguarding patient data. This includes how that data should be handled, maintained, and transmitted.
- Enforcement Rule. This rule provides guidelines with which companies investigate compliance violations.
How to Become HIPAA Compliant?
Steps to become HIPAA Compliant:
- Create a Security and Privacy Policy
- Name a Privacy and Security Officer
- Regularly Conduct a risk assessment.
- Implement Security Safeguards
- Business associate agreement management
- Breach Notification to be Instituted
- Documentation
- Create a Specific Policy for Email
- Create a Specific Mobile Policy
- Train Your Staff
Here are more details on how to become HIPAA compliant in a few steps:
- Create a Security and Privacy Policy
As said by Becker’s Hospital Review, “Healthcare organizations must develop, adopt and implement privacy and security policies and procedures,” “They must also make sure that they are documenting all their policies and procedures, including steps to take when a breach occurs.”
Turning out to be HIPAA compliant requires more than basically following Security and Protection Rules. Covered entities and business associates should demonstrate that they’ve been proactive about preventing HIPAA violations by making protection and security approaches.
In recent times data breach has grown, and it is crucial to have air-tight security safeguards. It is also imperative to have proper protocols in place to prevent any hack or breach.
It is required by healthcare organizations to maintain and distribute an NPP ( Notice of Privacy Practices ) form to patients, which needs to be filled out and signed by them.
The NPP should provide the covered entity’s privacy policies. It should include how PHI is handled and tell them about their right to access copies of their medical records.
- Name a Privacy and Security Officer
Every healthcare organization requires its own internal HIPAA experts as HIPAA legislation is complicated and it is ever-changing.
Keeping your data safe, secure, and, most importantly, confidential is an integral part of HIPAA.
Having a person or people in charge (HIPAA Security and privacy officer) who is an expert in the field is crucial. They will annually update and implement new policies. They can maintain air-tight policies and implement the best procedures at the time of an attack or breach.
The HIPAA Protection Officer is additionally answerable for looking after NPPs, overseeing and refreshing BAAs, planning instructional courses and self-reviews, and in any case guaranteeing that the association is consistent with this Privacy Rule.
The Security Officer builds up shields needed by the Security Rule and directs hazard appraisals to measure their adequacy.
- Regularly conduct risk Assessments.
Becoming HIPAA compliant is not a one-day process. It is a lengthy and regular process. You will have to check and keep track of your risk exposure daily. If not daily, it has to be checked annually. Anything not following the proper order needs to be corrected.
Regular checks on all administrative, technical, and physical safeguards to identify compliance gaps are necessary. A single, small mistake can cause massive problems if not attended to immediately and adequately.
- Implement Security Safeguards
Three types of safeguards are required by the security rule that covered entities, and business associates must have in place to secure ePHI — including:
- Administrative Safeguards: Organisations should report security management processes, assign security staff, receive data access to the executive’s framework, give the labor force security preparation, and intermittently survey all security conventions.
- Physical Safeguards: Organisations should have the option to control who approaches actual offices where ePHI is put away. They should likewise get all workstations and gadgets that store or communicate ePHI.
- Technical Safeguards: Associations should approach controls to tie down ePHI in the EHR and different data sets to guarantee representatives just see the information they’re approved to see. Information should be scrambled when it is very still and during travel, making the requirement for secure email, HIPAA Consistent Messaging, and HIPAA Agreeable Informing arrangements. Associations should likewise have review controls for all equipment and programming that oversee or communicate ePHI to guarantee they meet HIPAA network prerequisites. Also, there should be trustworthiness controls to guarantee ePHI isn’t inappropriately altered or erased.
Business associate agreement management
Covered Entities should have “Satisfactory assurances before PHI is being shared with business Associates who are HIPAA-compliant so that data security is not compromised and the parties must enter a BAA. BAA must record any changes brought, as the business associate relationship, and update dynamic changes by maintaining records and annual reviewing.
You need to have a strong link with your business associates. If your associates aren’t a strong link, you have a problem.
The HIPAA breach notification rule needs covered entities and Business Associates to describe breaches to OCR to ensure that the patient is notified about the breach whose personal information was supposedly compromised.
HIPAA-beholden organizations must announce a document-based action plan that displays the organization’s steps to counter the situation and a documented breach notification process to announce that the organization will abide by the rule.
Breach notification protocol to be instituted
Violation of An HIPAA doesn’t mean that you can always get into trouble as an organization, but the breach should be proved to be an unintentional act, and the organization had strived in its capabilities to deter such breaches. The organization must report the breaches to safeguard itself from trouble.
As noted by Becker’s “The Risk of Harm Standard and the risk assessment test can be used to determine if a breach has occurred, If a breach has occurred, it is essential that the healthcare organization document the results of the investigation and notify the appropriate authorities.”
Documentation
Documentation of all these compliance efforts, including privacy and security policies risk, assessments and self-audits, limitation plans, and staff training sessions, must be compiled by the organization. The documentation will be reviewed by OCR during HIPAA audits and complaint investigations. HIPAA compliance is crucial for healthcare organizations, not only to safeguard the personal information of patients but also to protect the bottom line. Health Care providers must be informed about the procedures to become HIPAA compliant, to keep the data safe, and must constitute technical departments that can look after the documents with all seriousness.
Create specific policies for email
The HHS Office for Social liberties, or OCR, has expressed it needs to see client rules created to the specific circumstance, as shown by explicit portable and email arrangements. Curiously, it doesn’t state anyplace in the OCR guidelines that PHI should just be sent as well as gotten through encoded email. Yet, it merits bringing up that your email framework is HIPAA consistent and with the encryption, all things considered. Also, you can shield yourself from examinations with scrambled emails.
Email encryption is a generally quick, simple, and easy cycle to execute in this day and age, and numerous suppliers will offer it gratis. It’s mainly an opportunity to investigate. However, on the off chance that you conclude that email encryption isn’t ideal for you now, you should educate your patients that requesting records through email puts them in danger.
Create a Specific Mobile Policy
Cell phones are all over the place, and they get more ubiquitous every single year. Each side of the medical services world, among suppliers and patients, utilizes cell phones to browse email and sign in to profiles. Accordingly, it will significantly profit you to make a solid strategy to defend well-being information on cell phones, for example, cell phones and PCs, which are especially vulnerable to actual robbery. The arrangement should address additionally what happens when another gadget is added to or taken out from the organization.
Train Your Staff
While not every person in your group should be an industry driving master in the better details of this, it will become you if your staff is serenely acquainted with the fundamental boundaries of HIPAA. It has been shown on various occasions by various examinations that workers are reliably probably the greatest danger to an organization’s network protection – generally through an absence of information on the legitimate conventions. No one needs to be the reason for a HIPAA infringement, so it’s your most significant advantage to give preparation to any new individuals who join your staff and periodic audits (some say at regular intervals) to proceed with workers.
Elements of an Effective Compliance Program
The Office of the Inspector General (OIG) for the Department of Health and Human Services (HHS) delivered a consistent preparing guide and set up “The Seven Central Components of a Powerful Compliance Program.” These are the seven core values that you should use to drive your consistency endeavors, and an evaluator utilizes these measures during examinations:
- Actualizing composed arrangements, methods, and principles of direction.
- Assigning a consistent official and consistent advisory group.
- Directing powerful preparing and schooling.
- Creating successful lines of correspondence.
- Leading inside observing and reviewing.
- Implementing principles through all-around advanced disciplinary rules.
- Reacting immediately to identified offenses and undertaking the remedial activity.
How Can Cloudanix Help?
Cloudanix helps you audit your AWS account by running rules that tell you if you are violating HIPAA compliance and remediation rules that help you fix these vulnerabilities. To know more about how Cloudanix helps you be HIPAA compliant, check this out. And if you are convinced, you can sign up!