CASB, CSPM, SEIM: Do you know what role they play in operating your Cloud workloads?

Not long ago, when IT companies were into storing all their data on-premise, clouds were just white, cotton-like things floating in the sky. With the recent uproar about cloud computing, clouds are now condensed with your data. The advantages are overflowing, first is its accessibility. Using the cloud gives access to your files from anywhere with an internet connection. Next is the recovery of data. In case a hard drive failure or any other hardware malfunction occurs, your files can be accessed on the cloud. It can be thought of as a backup solution for all the local storage on physical storage.
Lastly, the best part about cloud storage is strong security. Cloud storage has additional layers of security for these services. There are many people with important/private data stored on the cloud, these services make sure there is tight security. They make sure your files can not and do not get accessed by someone without proper verification.
Let us learn about some importance terms before diving into the security tools
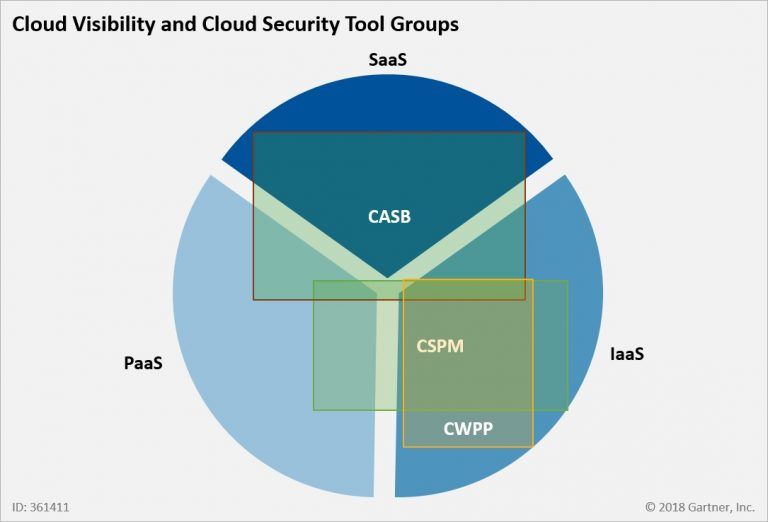
- IaaS: cloud-based services, services such as storage, networking, and virtualization.
- PaaS: hardware/software tools available over the internet.
- SaaS: third-party software over the internet.
- On-premise: software that’s installed in the same infrastructure as the enterprise.
The most commonly thrown words when it comes to Cloud Security are, CASB, CSPM, and SIEM. Might sound gibberish to some, but these play an extremely vital role when it comes to protecting your cloud workspace. Let us see how exactly these security protocols are established.
CASB or Cloud Access Security Broker
In the simplest terms, the CASB is a software tool that is the intermediary between an organization’s on-premises infrastructure and a cloud provider’s infrastructure. It primarily secures data flowing to and fro in the on-premise IT architecture and cloud environment. It uses the organization’s security policies. CASB majorly protects the enterprise systems from cyberattacks. It implements malware prevention and provides data security through encryption schemes. It makes data streams incomprehensible to outside parties. In a nutshell, CASB takes care of multiple types of security policies such as authentication, single sign-on, authorization, credential mapping, device profiling, encryption, tokenization, logging, alerting, malware detection/prevention, etc.
The Main Features of CASB are
Visibility
Enterprises need visibility for their cloud account usage. It includes monitoring who uses the cloud apps, the different departments, from which location, and also the devices used.
BYOD, Shadow IT, and Increased Cloud Usage
BYOD is the new concept of Bring Your Own Device. With the growing popularity of SaaS and cloud apps, restricting cloud app access to a defined set of endpoints has become a mandatory yet tough task. CASB aids in enforcing access policies to identify and categorize cloud apps in the given organization.
Threat Protection and Data Security
Guarding against the malicious intent or negligence of authorized users is one of the main features of CASB. It detects suspicious behavior. Further, it blocks unauthorized access, thus protecting your data.
Compliance
Organizations ensure that they are compliant with different regulations that ensure data privacy and security. CASB helps in ensuring compliance with regulations like SOX and HIPAA. It further helps to benchmark your security configurations.
CSPM or Cloud Security Posture Management
CSPM or Cloud Security Posture Management automatically assesses the cloud environment and identifies security violations. It further provides the steps required to remediate them. This is often accomplished through automation. It is highly recommended for security and risk management officials to invest in CSPM tools. These tools are indispensable when it comes to avoiding misconfigurations that lead to data leakage. This is a relatively new set of tools. However, CSPM is majorly used for the management of cloud security. The continuously emerging changes in the cloud environment make it difficult to keep track of whether or not your data is stored safely.
As the cloud grows larger, the need to protect and monitor against misconfigurations grows simultaneously. CSPM allows tracking. This can be achieved through automation. Few queries are run periodically where the frequency is dependent on the CSPM tool we are using. The features allow automatic alerting to security administrators who can get to the root of the problem and solve it as soon as it arises. CSPM activates the capability to view compliances along with frameworks. For example, CIS v1.1, HIPAA, or SOC2. These strengthen the cloud data security and also increase the confidence in the organization’s product and overall security.
A few of the prominent security features of CSPM are
- Identify Access
- Asset Inventory and Classification
- Compliance Policy Monitoring and Assessment
- Operational Monitoring
- Incident Response
- Risk Identification and Visualization
SIEM or Security Information and Event Management
This software/tool has been useful various for over a decade. SIEM solutions provide an overall view of what is exactly happening on the applied network in real-time. It helps IT teams ensure more proactive action when subjected to security threats. SIEM solutions are unique in the way that it combines Security Event Management (SEM) with Security Information Management (SIM). SEM is responsible for the analysis of the event and log data in real-time as well as threat management. Whereas SIM is responsible for retrieving and analyzing log data and later generates a report. SIEM solutions ensure complete visibility and control over what is happening over the network in real-time.
The Best Features of SIEM are
- Reduces the time it takes to identify threats, further minimizes the damage from those threats.
- Can be used by companies for a variety of cases revolving around data. These might include various security programs, audit and compliance reports, help desk as well as network troubleshooting;
- Supports large quantities of data so organizations. It can further continue to increase its data capacity.
- Supplies information on threat detection and security alerts.
- Can produce a detailed forensic analysis during any major security breaches.
SIEM comes across a whole package for an enterprise. It can be used to locate a threat, combat any security breach, and also generate a detailed report on the breach, for educational purposes. It locates threats in real-time, thus making it more convenient and easy to eradicate them. If you are looking forward to securing your data, identifying and neutralizing cyberattacks SIEM investment is a must.
On the other hand, if your organization is dealing with sensitive data in SaaS, a CASB can be activated. The enterprise can extend workload protection to the cloud with CASB.
If your organization is more into processing sensitive data using a public cloud, invest in CSPM to monitor the cloud configuration. Cloud workload protection keeps your workloads moving across different cloud environments safe. It must be entirely functional for any cloud-based application to work well. The working efficiency must be maintained without tolerating any security risks. All these tools make your cloud environment a safer place for all your work.
Why Cloudanix?
Your Cloud infrastructure is Multi-Clouds, Multiple Accounts, and Multi-Regions used by multiple team members. It requires continuous attention to Security, Compliance, drift, Real-time activities, and Data Leakages. Cloudanix gives you security monitoring + remediation workflows to stay secure. Cloudanix is the Central Dashboard for your Security, Cloud-Ops, and Engineering teams to manage Security where “Multi” is a pain.